First, list the content of the zip file
$ unzip -vl bomb.zip
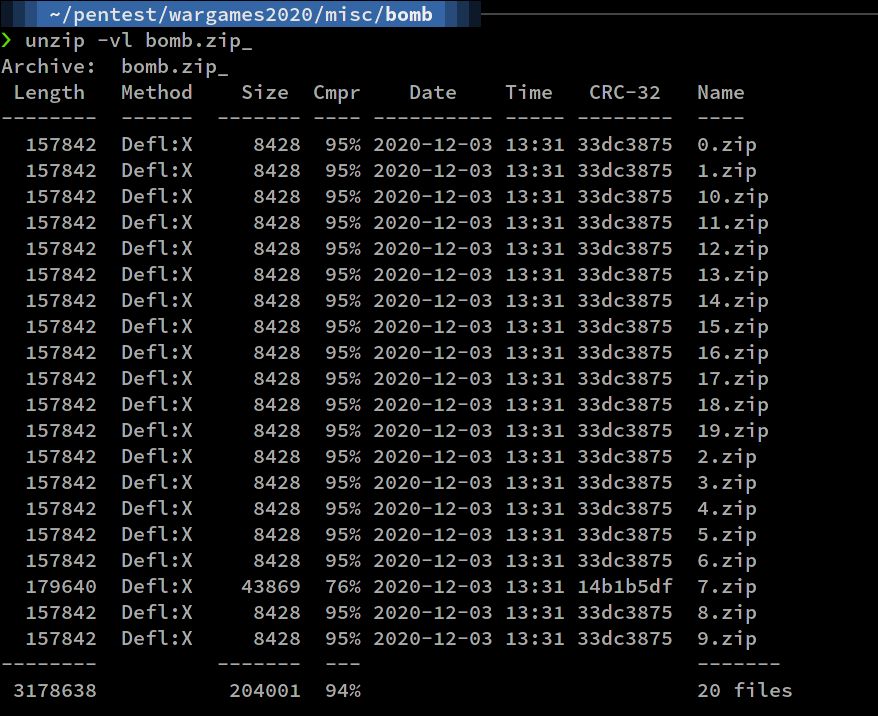
Notice that one of the CRC32 value is different. We need to extract that single file.
$ unzip bomb.zip 7.zip
Next, repeat the steps above with the new archive that you just got until you get to this point:
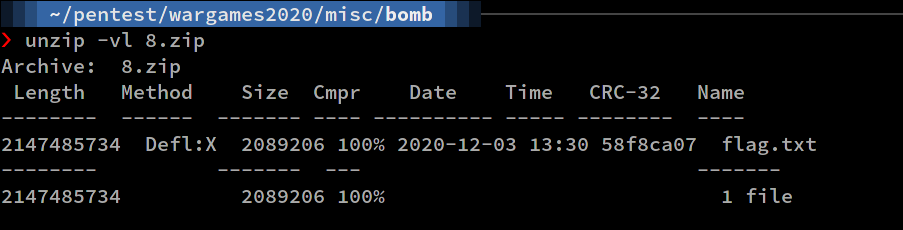
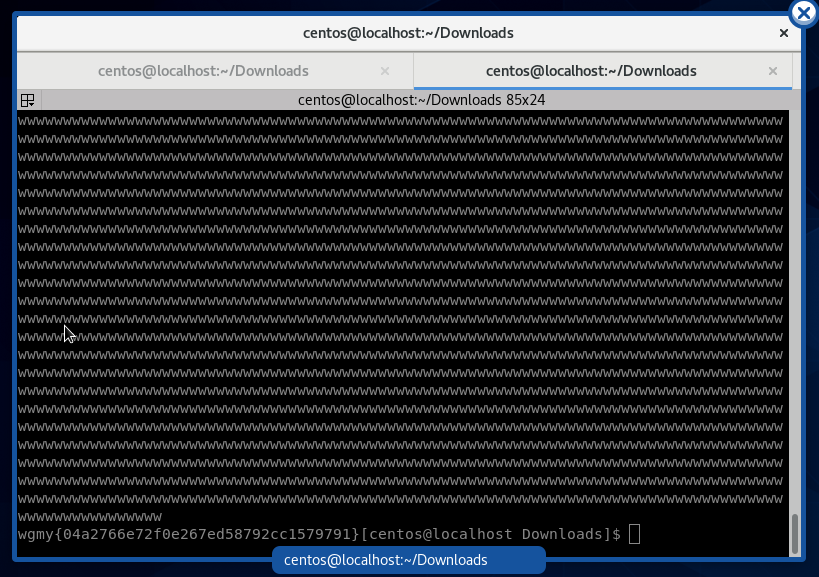
I was unsure what to do at this point because I thought this was another bomb, so I transferred this file into a VM and extracted it. Turns out it was not. Then I executed strings flag.txt in the terminal, but it turns out the whole file is a string. Actually the flag is at the end of the file. I discovered this by using the tail command
$ tail flag.txt
It will throw out a long string of ‘w‘, but in the end you will get your flag.
Source:
https://github.com/ctfs/write-ups-2015/tree/master/asis-quals-ctf-2015/forensic/keka-bomb ASIS Quals CTF 2015: Keka Bomb